Re: Allowing Anonymous FTP Connections
by Jesse Burkhardt - 2001/09/01
The "disabling" anonymous connections generates a counter-intuitive MS warning that encryption will be turned off and security compimised. The following suggests to me that "Allow Anonymous Connections" should be enabled if FTP service is to be used at all. However, there are completely contradictory recommendations sprinkled throughout Deja - the last entry excerpted has anonymous connections disabled. Obviously the best thing to do for maximum security is simply to stop the FTP service from running.
A couple of links worth visiting 1) Collaborative Computational Project Number 14 mostly for discussion, and 2) Tera Term Home Page, which provides a free secure FTP tool for Windows.
First of all, let me clarify that the "anonymous" user account for FTP service is analogous to the IUSR account for web service access. In fact, looking at the Security Accounts tab of the Default FTP Site Properties panel (from the IIS console), MS actually references the IUSR as the user for anonymous FTP connections. look at the following sceenshots:
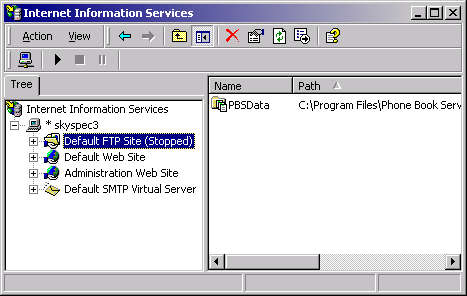
Right click the highlighted Default FTP Server entry to bring up the following panel:
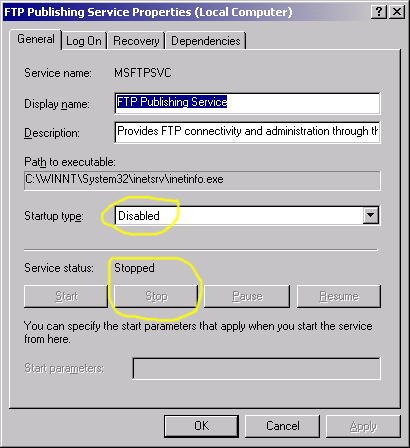
Another FTP security hole may be plugged up through setting the FTP Publishing Service.
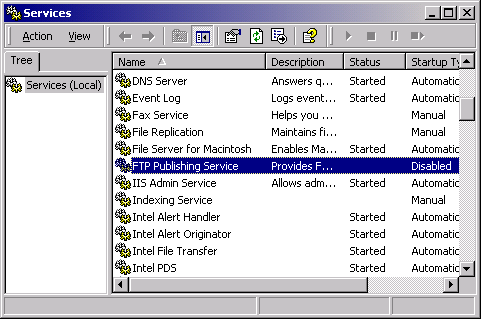
Right click the highlighted FTP Pushing Service entry to bring up the following panel:
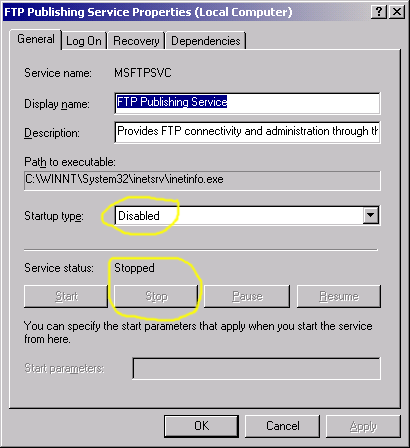
From a Deja entry:
Beware, if FTP Service is running, anyone can log onto your machine using a any valid account, unless you have checked the Allow Only Anonymous Connections option. If someone were to log on using an admin account, he would have full access on the partition(s) allowed by FTP Security.
Another Deja warning:
Under default installation of Windows NT systems, Guest is granted permissions for all types of access on the system. This could easily be a security hole and it is recommended that wary administrators turn off this switch.
More from Deja:
If you set "Allow only anonymous connections", then "anonymous" will be the only valid logon account that will work using ftp. This is more secure, because NT by default uses end-to-end encryption to hide password authentification (which supposedly nobbles anyone with a MAC sniffer on your LAN), where as vanilla ftp doesn't. This stops people connecting to your ftp server using their LAN accounts and passwords, and therefore prevents unhelpful individuals from capturing packets and acquiring passwords, which is easy to do with TCP.
Another Entry (steps to create a specific FTP user account - this is the simple version, a more sophisticated procedure immediately follows this one):
If you wish to enable an FTP authentication method, do the following:
- Create a Windows user account appropriate for the authentication method. If appropriate, add the account to a Windows user group.
- Configure NTFS permissions for the directory or file for which you want to control access.
- In the Internet Information Services snap-in, select a site, directory, or file, and open its property sheets.
- Select the Security Accounts property sheet. Select the Allow Anonymous Connections check box.
- In the Username and Password text boxes, enter the anonymous logon user name and password you want to use. The user name is the name of the
anonymous user account and is typically designated as IUSR_computername. If the Allow IIS to control password check box is selected, you need to clear it to change the password.
- Select the Allow IIS to control password check box to match passwords
with Windows user accounts.
- Select the Allow only anonymous connections check box to require all
users to log on as anonymous users.
- Click OK.
- Set appropriate NTFS permissions for the anonymous account.
A more detailed set of instructions to restrict FTP Access without making users members of Administrators group:
It is rather tricky. Here is how, if the FTP server happens to be a Win2000 AD-enabled domain controller:
I. On the server:
First enable Log On Locally:
- Open Active Directory Users And Computers.
- If you have not already created appropriate users and/or groups, do that now. If you've put everyone into Administrators, take them back out.
- Select Domain Controllers and right-click it to open Properties.
- Click the Group Policy tab.
- Click the Default Domain Controllers Policy, and click Edit.
- Expand Computer Config., then expand Windows Settings, then expand
Security Settings then expand Local Policies.
- Click User Rights Assignments.
- In the right pane, double-click Log On Locally.
- Add your user or group, and click OK until all windows are closed.
II. Second, set FTP security:
- Start Internet Services Manager.
- Open the Properties of the FTP site.
- Disable "Allow Anonymous Connections".
- Click OK until all windows are closed.
III. Third, set NTFS security (assuming the site root is on an NTFS volume -- which is highly recommended):
- Start Windows Explorer.
- Navigate to the FTP root folder.
- Open its Properties and click the Security tab.
- Add the users or group you want to have access.
- Configure their permissions.
- Remove all other users and groups (although you may want to leave
Administrators, with Full Control ;^) }.
- If you choose, click Advanced and allow inheritance.
- Click OK until all windows are closed.
IV. Now...On the client:
- Connect to the FTP site by whatever means (ftp:// in browser; FTP at a command prompt; ...)
- At the logon prompt, enter the user logon without the domain portion.
Example: If Win2000 user logon name is M@there.com then you would enter just M.
- Enter the account password.
- Voila! The account will have the most restrictive permissions results from IIS-FTP and NTFS.




